1. Install Anti-Virus Software
-This should not even have to be listed, if you don’t have anti-virus software installed, you’re asking for trouble! And if your reason for not installing anti-virus software is because it’s too expensive, then that can reason can be shot down because there are several free anti-virus programs out there that are considered better than commercial software packages. Here are two of the most popular ones:
AVG Anti-Virus – Very good and completely free.
Avast Anti-Virus – Almost on par with AVG.
Kaspersky Anti-Virus – Not free, but one of the best detection rates.
2. Update All Software
- Installing an anti-virus program by itself is not enough. There are hundreds of new threats that are found daily and the anti-virus programs release updates regularly to combat the new threats. Make sure you anti-virus program is set to update automatically so that you don’t have to rely on your memory to do it.
Also, this goes for all the software on your computer. The most important software to keep up to date is your Windows operating system. It is essential to have Automatic Updates turned on and set to download and install updates automatically.
3. Install only Trusted Software
- If you’re not sure what a piece of software does from it’s name, then don’t install it. Also, don’t install anything you didn’t intend to install in the first place. Sometimes programs will ask you to install other programs during the install of the first application. Be careful of that because it’s usually spyware. Install software from big names sites only, such as Microsoft or Adobe.
4. Avoid P2P File Sharing Software
– If used with great caution, P2P software is quite useful for movies, songs and software, but if you’re not very technically savvy, you might end up downloading a song that has a keystroke logger attached to it that will send anything you type to some other computer over the Internet. It’s almost impossible to tell that this is occurring unless your anti-virus or anti-spyware programs pick it up in their scans.
5. Delete Unknown Emails
– If you receive emails from random people’s names, do not bother to open the email, just delete it. If you have any doubts after reading the name and the subject, it’s probably not someone you know. Never download or open attachments unless you are sure it’s from someone you know. Give the person a call quickly and ask them if you’re not sure. Most large companies that you create online accounts with will not send you attachments unless you specifically ask for them through their web site. Also, be wary of any emails from sites pretending to be banks, auction sites, etc asking for you to verify bank account info or address info. No bank ever does that.
6. Do not click on Ads
- Avoid clicking on ads if you can. Especially those ads where something is flying around and if you shoot the duck, you win some prize! Ads have become more sophisticated in that they try to make the ad interactive so that you’ll be tempted to play it like a game.
7. Run Virus Scans Regularly
– If you’re not in the mood to scan every day, at least run a scan once a week. Actually, setup a schedule for your computer in your anti-virus software to run a scan late at night or whenever you don’t use your computer and that way you won’t be bothered with a slow computer.
8. Be careful what you attach to your computer
– This is a more common way to transfer viruses than you might think. Everyone now has a USB flash stick that they carry around on their key chains, ready to snap into any computer. But who knows what your viruses are on your friends computers and what accidentally got transferred to their USB stick. A lot of virus programs will auto launch right when the USB stick is put into the computer, so you don’t even have to open or download any of the files to be infected.
9. Avoid Shady Web Sites
– If you need to look at porn, then make sure you do it in a virtual environment. You are DEFINITELY going to get some virus or spyware if you browse porn sites on your computer. Virtualization basically allows you to run programs like Internet Explorer in a virtual environment that does not effect your current operating system. If you want to find out more, search for “Virtual PC” or “VM Ware” in Google. Otherwise, simply avoid going to shady web sites!
10. Turn On or Install a Firewall
- If you’re running Windows XP, make sure Windows Firewall is turned on. A firewall prevents hackers from gaining access to your computer by limiting the number of ports that are open to the public. Also, when buying a wireless router, make sure it has a built in firewall. Having a software and hardware firewall is better than just having one or the other.
11. Secure Your Wireless Network
– Most wireless routers are set to no security when you install them. Be sure to log into the router and at least set the basic security that requires a password. There are stronger encryption options, but if you don’t understand those, then simply set a password on the router, otherwise anyone can connect to your home network and access everything.
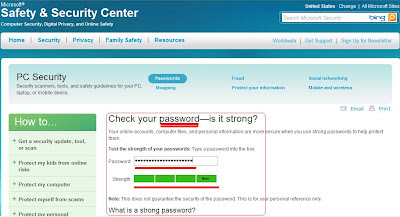
12. Use a Complex Password for Login
– This means that you should already have a password to login to your computer. Not having a password at all is not a good idea. Create a password for all user accounts and make sure it’s complex. Complex means it should have numbers, upper case characters, lower case characters, and symbols. This makes it way more difficult for a hacker to get into your computer.
------------------------------------------------------------------------------
How to boost your malware defense and protect your PC
Free computer protection to help secure your computer against malware:
Build up your computer's defenses
Do not be tricked into downloading malware
Build up your malware defenses
Install antivirus and antispyware programs from a trusted source
Never download anything in response to a warning from a program you didn't install or don't recognize that claims to protect your PC or offers to remove viruses. It is highly likely to do the opposite.
Get reputable anti-malware programs from a vendor you trust.
Microsoft Security Essentials offers free real-time protection against malicious software for your PC.
Or, choose from a list of Microsoft partners who provide anti-malware software.
Update software regularly
Cybercriminals are endlessly inventive in their efforts to exploit vulnerabilities in software, and many software companies work tirelessly to combat these threats.
That is why you should:
Regularly install updates for all your software—antivirus and antispyware programs, browsers (like Windows Internet Explorer), operating systems (like Windows), and word processing and other programs.
Subscribe to automatic software updates whenever they are offered—for example, you can automatically update all Microsoft software.
Uninstall software that you don't use. You can remove it using Windows Control Panel.
Use strong passwords and keep them secret
Strong passwords are at least 14 characters long and include a combination of letters, numbers, and symbols. Find out how to create them.
Don't share passwords with anyone.
Don’t use the same password on all sites. If it is stolen, all the information it protects is at risk.
Create different strong passwords for the router and the wireless key of your wireless connection at home.
Find out how from the company that provides your router.
Never turn off your firewall
A firewall puts a protective barrier between your computer and the Internet.
Turning it off for even a minute increases the risk that your PC will be infected with malware.
Use flash drives cautiously
Minimize the chance that you'll infect your computer with malware:
Don't put an unknown flash (or thumb) drive into your PC.
Hold down the SHIFT key when you insert the drive into your computer.
If you forget to do this, click in the upper-right corner to close any flash drive-related pop-up windows.
Don't open files on your drive that you're not expecting.
Don't be tricked into downloading malware
Instead, follow this advice:
Be very cautious about opening attachments or clicking links in email or IM, or in posts on social networks (like Facebook)—even if you know the sender. Call to ask if a friend sent it; if not, delete it or close the IM window.
Avoid clicking Agree, OK, or I accept in banner ads, in unexpected pop-up windows or warnings, on websites that may not seem legitimate, or in offers to remove spyware or viruses.
Instead, press CTRL + F4 on your keyboard.
If that doesn’t close the window, press ALT + F4 on your keyboard to close the browser. If asked, close all tabs and don’t save any tabs for the next time you start the browser.
Only download software from websites you trust. Be cautious of "free" offers of music, games, videos, and the like. They are notorious for including malware in the download.