Remove Trovi.com redirect (Virus Removal Guide)
Trovi.com is a browser
hijacker, which is promoted via other free downloads, and once installed
it will change your browser homepage and default search engine to trovi.com.
![Trovi.com virus [Image: Trovi.com virus]](http://malwaretips.com/blogs/wp-content/uploads/2014/01/trovi-com-virus.jpg)
The Trovi.com homepage will display advertisements and sponsored links in your search results, and may collect search terms from your search queries. The Trovi.com hijack is used to boost advertising revenue, as in the use of blackhat SEO, to inflate a site’s page ranking in search results.
Trovi.com it’s technically not a virus, but it does exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program.
Trovi.com is an ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer (BHO) and Firefox/Chrome (plugin) and distributed through various monetization platforms during installation. The browser extension includes various features that will modify the default or custom settings of the browser including the home page, search settings and in some cases will modify Internet Explorer’s load time threshold, place a lock file within Firefox to prevent competing software from changing its settings as well as disable the browser’s Content Security Policy in order to allow for cross site scripting of the plugin.
Trovi.com homepage got on your computer after you have installed a freeware software (video recording/streaming, download-managers or PDF creators) that had bundled into their installation this browser hijacker.
For example, when you install “Youtube Downloader HD”, you will also agree to change your browser homepage and default search engine to trovi.com.
![Trovi.com redirect [Image: Trovi.com redirect]](http://malwaretips.com/blogs/wp-content/uploads/2014/01/trovi-com-redirect.jpg)
However when you uninstall “Youtube Downloader HD” from your computer, your web browser’s default settings will not be restored. This means that you’ll have to remove Trovi.com homepage from your favorite web browser manually.
You should always pay attention when installing software because often, a software installer includes optional installs, such as this Trovi.com browser hijacker. Be very careful what you agree to install.
Always opt for the custom installation and deselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place. It goes without saying that you should not install software that you don’t trust.
It is important to note that Malwarebytes Anti-Malware works well and should run alongside antivirus software without conflicts.
Your computer should now be free of the Trovi.com infection. If your current anti-virus solution let this infection through, you may want to consider purchasing the Premium version of Malwarebytes Anti-Malware to protect against these types of threats in the future.
If you are still experiencing problems while trying to remove Trovi.com hijacker from your machine, please start a new thread in our Malware Removal Assistance forum.
![Trovi.com virus [Image: Trovi.com virus]](http://malwaretips.com/blogs/wp-content/uploads/2014/01/trovi-com-virus.jpg)
The Trovi.com homepage will display advertisements and sponsored links in your search results, and may collect search terms from your search queries. The Trovi.com hijack is used to boost advertising revenue, as in the use of blackhat SEO, to inflate a site’s page ranking in search results.
Trovi.com it’s technically not a virus, but it does exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program.
Trovi.com is an ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer (BHO) and Firefox/Chrome (plugin) and distributed through various monetization platforms during installation. The browser extension includes various features that will modify the default or custom settings of the browser including the home page, search settings and in some cases will modify Internet Explorer’s load time threshold, place a lock file within Firefox to prevent competing software from changing its settings as well as disable the browser’s Content Security Policy in order to allow for cross site scripting of the plugin.
Trovi.com homepage got on your computer after you have installed a freeware software (video recording/streaming, download-managers or PDF creators) that had bundled into their installation this browser hijacker.
For example, when you install “Youtube Downloader HD”, you will also agree to change your browser homepage and default search engine to trovi.com.
![Trovi.com redirect [Image: Trovi.com redirect]](http://malwaretips.com/blogs/wp-content/uploads/2014/01/trovi-com-redirect.jpg)
However when you uninstall “Youtube Downloader HD” from your computer, your web browser’s default settings will not be restored. This means that you’ll have to remove Trovi.com homepage from your favorite web browser manually.
You should always pay attention when installing software because often, a software installer includes optional installs, such as this Trovi.com browser hijacker. Be very careful what you agree to install.
Always opt for the custom installation and deselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place. It goes without saying that you should not install software that you don’t trust.
How to remove Trovi.com (Virus Removal Guide)
This page is a comprehensive guide, which will remove Trovi.com from your Internet Explorer, Firefox and Google Chrome.
Please perform all the steps in the correct order. If you have any questions or doubt at any point, STOP and ask for our assistance.
STEP 1: Remove Trovi.com browser hijacker from your computer with AdwCleaner
STEP 2: Remove Trovi.com from Internet Explore, Firefox and Google Chrome with Junkware Removal Tool
STEP 3: Remove Trovi.com malicious files with Malwarebytes Anti-Malware Free
STEP 4: Double-check for the Trovi.com infection with HitmanPro
Please perform all the steps in the correct order. If you have any questions or doubt at any point, STOP and ask for our assistance.
STEP 1: Remove Trovi.com browser hijacker from your computer with AdwCleaner
STEP 2: Remove Trovi.com from Internet Explore, Firefox and Google Chrome with Junkware Removal Tool
STEP 3: Remove Trovi.com malicious files with Malwarebytes Anti-Malware Free
STEP 4: Double-check for the Trovi.com infection with HitmanPro
STEP 1: Remove Trovi.com browser hijacker with AdwCleaner
The AdwCleaner utility will scan your computer and web browser for malicious files, adware browser extensions and registry keys, that may have been installed on your computer without your knowledge.- You can download AdwCleaner utility from the below link.
ADWCLEANER DOWNLOAD LINK (This link will automatically download AdwCleaner on your computer) - Before starting AdwCleaner, close all open programs and internet browsers, then double-click on the AdwCleaner icon.

If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run. - When the AdwCleaner program will open, click on the “Scan” button as shown below.

AdwCleaner will now start to search for the “Trovi.com” malicious files that may be installed on your computer. - To remove the “Trovi.com” malicious files that were detected in the previous step, please click on the “Clean” button.

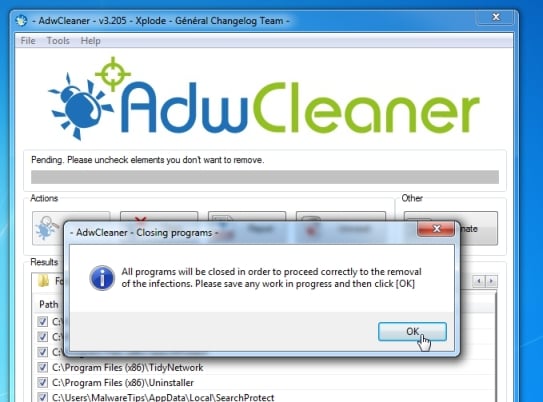
- AdwCleaner will now prompt you to save any open files or documents, as the program will need to reboot the computer. Please do so and then click on the OK button.
STEP 2: Remove Trovi.com from Internet Explore, Firefox and Google Chrome with Junkware Removal Tool
Junkware Removal Tool is a powerful utility, which will remove Trovi.com extensions from Internet Explorer, Firefox and Google Chrome.- You can download the Junkware Removal Tool utility from the below link:
JUNKWARE REMOVAL TOOL DOWNLOAD LINK (This link will automatically download the Junkware Removal Tool utility on your computer) - Once Junkware Removal Tool has finished downloading, please double-click on the JRT.exe icon as seen below.
![Double-click on the Junkware Removal Tool utility [Image: Junkware Removal Tool]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Junkware-icon.jpg)
If Windows prompts you as to whether or not you wish to run Junkware Removal Tool, please allow it to run. - Junkware Removal Tool will now start, and at the Command Prompt, you’ll need to press any key to perform a scan for the Trovi.com virus.
![Junkware Removal Tool scanning for Trovi.com virus [Image: Junkware Removal Tool scanning for Trovi.com homepage]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/junkware-removal-tool.jpg)
Please be patient as this can take a while to complete (up to 10 minutes) depending on your system’s specifications. - When the scan Junkware Removal Tool will be completed, this utility
will display a log with the malicious files and registry keys that were
removed from your computer.
![Junkware Removal Tool final log [Image: Junkware Removal Tool final log]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Junkware-log.jpg)
STEP 3: Remove Trovi.com malicious files from your computer with Malwarebytes Anti-Malware Free
Malwarebytes Anti-Malware Free uses industry-leading technology to detect and remove all traces of malware, including worms, Trojans, rootkits, rogues, dialers, spyware, and more.It is important to note that Malwarebytes Anti-Malware works well and should run alongside antivirus software without conflicts.
- You can download download Malwarebytes Anti-Malware from the below link.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK (This link will open a new web page from where you can download Malwarebytes Anti-Malware Free) - Once downloaded, close all programs, then double-click on the icon on your desktop named “mbam-setup-consumer-2.00.xx” to start the installation of Malwarebytes Anti-Malware.
![Malwarebytes Anti-Malware setup program [Image: Malwarebytes Anti-Malware setup program]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/Malwarebytes-Anti-Malware-Setup.jpg)
 You may be presented with a User Account Control dialog asking you if
you want to run this file. If this happens, you should click “Yes” to continue with the installation.
You may be presented with a User Account Control dialog asking you if
you want to run this file. If this happens, you should click “Yes” to continue with the installation. - When the installation begins, you will see the Malwarebytes Anti-Malware Setup Wizard which will guide you through the installation process.
![Malwarebytes Anti-Malware Setup Wizard [Image: Malwarebytes Anti-Malware Setup Wizard]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-2-0-installation.jpg)
To install Malwarebytes Anti-Malware on your machine, keep following the prompts by clicking the “Next” button.
![Malwarebytes Anti-Malware Final Setup Screen [Image: Malwarebytes Anti-Malware Final Setup Screen]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-2-0-final-screen.jpg)
- Once installed, Malwarebytes Anti-Malware will automatically start
and you will see a message stating that you should update the program,
and that a scan has never been run on your system. To start a system
scan you can click on the “Fix Now” button.
![[Image: Click on the Fix Now button to start a scan]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-fix-now.jpg)
Alternatively, you can click on the “Scan” tab and select “Threat Scan“, then click on the “Scan Now” button.
![Malwarebytes Anti-Malware Threat Scan [Image: Malwarebytes Anti-Malware Threat Scan]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-threat-scan-option.jpg)
- Malwarebytes Anti-Malware will now check for updates, and if there are any, you will need to click on the “Update Now” button.
![Click on Update Now to update Malwarebytes Anti-Malware [Image: Click on Update Now to update Malwarebytes Anti-Malware]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-2-0-update-now.jpg)
- Malwarebytes Anti-Malware will now start scanning your computer for
the Trovi.com virus. When Malwarebytes Anti-Malware is scanning it will
look like the image below.
![Malwarebytes Anti-Malware while performing a scan [Image: Malwarebytes Anti-Malware while performing a scan]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-scan.jpg)
- When the scan has completed, you will now be presented with a screen
showing you the malware infections that Malwarebytes’ Anti-Malware has
detected. To remove the malicious programs that Malwarebytes
Anti-malware has found, click on the “Quarantine All” button, and then click on the “Apply Now” button.
![Remove the malware that Malwarebytes Anti-Malware has detected [Image: Remove the malware that Malwarebytes Anti-Malware has found]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-potential-threat-detected.jpg)
Please note that the infections found may be different than what is shown in the image. - Malwarebytes Anti-Malware will now quarantine all the malicious
files and registry keys that it has found. When removing the files,
Malwarebytes Anti-Malware may require a reboot in order to remove some
of them. If it displays a message stating that it needs to reboot your
computer, please allow it to do so.
![Malwarebytes Anti-Malware asking to reboot your computer [Image: Malwarebytes Anti-Malware while removing viruses]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-remove-virus.jpg)
After your computer will restart, you should open Malwarebytes Anti-Malware and perform another “Threat Scan” scan to verify that there are no remaining threats
STEP 4: Double check for the Trovi.com infection with HitmanPro
HitmanPro is a second opinion scanner, designed to rescue your computer from malware (viruses, trojans, rootkits, etc.) that have infected your computer despite all the security measures you have taken (such as anti virus software, firewalls, etc.). HitmanPro is designed to work alongside existing security programs without any conflicts. It scans the computer quickly (less than 5 minutes) and does not slow down the computer.- You can download HitmanPro from the below link:
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download HitmanPro) - Double-click on the file named “HitmanPro.exe” (for 32-bit versions of Windows) or “HitmanPro_x64.exe” (for 64-bit versions of Windows). When the program starts you will be presented with the start screen as shown below.
![HitmanPro startup screen (Click Next) [Image: HitmanPro start-up screen]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-install.jpg)
Click on the “Next” button, to install HitmanPro on your computer.
![HitmanPro installation options (Click Next) [Image: HitmanPro setup options]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmapro-start-scan.jpg)
- HitmanPro will now begin to scan your computer for Trovi.com malicious files.
![HitmanPro scanning for Trovi.com Ads [Image: HitmanPro scanning for malware]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-scanning.jpg)
- When it has finished it will display a list of all the malware that
the program found as shown in the image below. Click on the “Next” button, to remove Trovi.com virus.
![HitmanPro scan results (Click Next) [Image: HitmanPro scan results]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-scan-results.jpg)
- Click on the “Activate free license” button to begin the free 30 days trial, and remove all the malicious files from your computer.
![Click on the Activate free license button [Image: HitmanPro Activate Free License]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-activation.jpg)
Your computer should now be free of the Trovi.com infection. If your current anti-virus solution let this infection through, you may want to consider purchasing the Premium version of Malwarebytes Anti-Malware to protect against these types of threats in the future.
If you are still experiencing problems while trying to remove Trovi.com hijacker from your machine, please start a new thread in our Malware Removal Assistance forum.





























