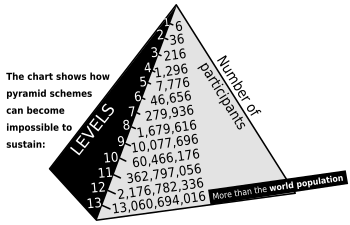
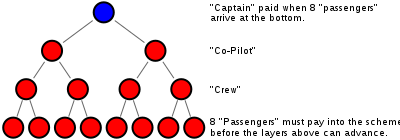
A pyramid scheme is an unsustainable business model that involves promising participants payment or services, primarily for enrolling other people into the scheme, rather than supplying any real investment or sale of products or services to the public.[1][2]
Various forms of pyramid schemes are illegal in many countries including Albania, Australia,[3][4] Austria,[5] Belgium,[6] Brazil, Canada, China,[7] Colombia,[8] Denmark, the Dominican Republic,[9] Estonia,[10]France, Germany, Hong Kong,[11] Hungary, Iceland, Iran,[12] Italy,[13] Japan,[14] Malaysia, Mexico, Nepal, the Netherlands,[15] New Zealand,[16] Norway,[17] the Philippines,[18] Poland, Portugal, Romania,[19]Russian Federation, South Africa,[20] Spain, Sri Lanka,[21] Sweden,[22] Switzerland, Taiwan, Thailand,[23] Turkey,[24] Ukraine,[25] the United Kingdom, and the United States.[26]
These types of schemes have existed for at least a century, some with variations to hide their true nature. Multilevel marketing plans have also been classified as pyramid schemes.[27][28][29][30]
Contents
[hide]Concept and basic models[edit]
In a pyramid scheme, an organization compels individuals to make a payment and join. In exchange, the organization promises its new members a share of the money taken from every additional member that they recruit. The directors of the organization (those at the top of the pyramid) also receive a share of these payments. For the directors, the scheme is potentially lucrative—whether or not they do any work, the organization's membership has a strong incentive to continue recruiting and funneling money to the top of the pyramid.
Such organizations seldom involve sales of products or services with real value. Without creating any goods or services, the only ways for a pyramid scheme to generate revenue are to recruit more members or solicit more money from current members. Eventually, recruiting is no longer possible and the plurality of members are unable to profit from the scheme.
The "Eight-Ball" model[edit]
Many pyramids are more sophisticated than the simple model. These recognize that recruiting a large number of others into a scheme can be difficult so a seemingly simpler model is used. In this model each person must recruit two others, but the ease of achieving this is offset because the depth required to recoup any money also increases. The scheme requires a person to recruit two others, who must each recruit two others, who must each recruit two others.
Prior instances of this scheme have been called the "Airplane Game" and the four tiers labelled as "captain", "co-pilot", "crew", and "passenger" to denote a person's level. Another instance was called the "Original Dinner Party" which labeled the tiers as "dessert", "main course", "side salad", and "appetizer". A person on the "dessert" course is the one at the top of the tree. Another variant, "Treasure Traders", variously used gemology terms such as "polishers", "stone cutters", etc. or gems like "rubies", "sapphires", "diamonds", etc.
Such schemes may try to downplay their pyramid nature by referring to themselves as "gifting circles" with money being "gifted". Popular schemes such as "Women Empowering Women"[31] do exactly this.
Whichever euphemism is used, there are 15 total people in four tiers (1 + 2 + 4 + 8) in the scheme—with the Airplane Game as the example, the person at the top of this tree is the "captain", the two below are "co-pilots", the four below are "crew," and the bottom eight joiners are the "passengers".
The eight passengers must each pay (or "gift") a sum (e.g., $5,000) to join the scheme. This sum (e.g., $40,000) goes to the captain who leaves, with everyone remaining moving up one tier. There are now two new captains so the group splits in two with each group requiring eight new passengers. A person who joins the scheme as a passenger will not see a return until they advance through the crew and co-pilot tiers and exit the scheme as a captain. Therefore, the participants in the bottom three tiers of the pyramid lose their money if the scheme collapses.
If a person is using this model as a scam, the confidence trickster would take the majority of the money. They would do this by filling in the first three tiers (with one, two, and four people) with phony names, ensuring they get the first seven payouts, at eight times the buy-in sum, without paying a single penny themselves. So if the buy-in were $5,000, they would receive $40,000, paid for by the first eight investors. They would continue to buy in underneath the real investors, and promote and prolong the scheme for as long as possible to allow them to skim even more from it before it collapses.
Although the "captain" is the person at the top of the tree, having received the payment from the eight paying passengers, once they leave the scheme they are able to re-enter the pyramid as a "passenger" and hopefully recruit enough to reach captain again, thereby earning a second payout.
Matrix schemes[edit]
Main article: Matrix scheme
Matrix schemes use the same fraudulent non-sustainable system as a pyramid; here, the participants pay to join a waiting list for a desirable product which only a fraction of them can ever receive. Since matrix schemes follow the same laws of geometric progression as pyramids, they are subsequently as doomed to collapse. Such schemes operate as a queue, where the person at head of the queue receives an item such as a television, games console, digital camcorder, etc. when a certain number of new people join the end of the queue. For example, ten joiners may be required for the person at the front to receive their item and leave the queue. Each joiner is required to buy an expensive but potentially worthless item, such as an e-book, for their position in the queue. The scheme organizer profits because the income from joiners far exceeds the cost of sending out the item to the person at the front. Organizers can further profit by starting a scheme with a queue with shill names that must be cleared out before genuine people get to the front. The scheme collapses when no more people are willing to join the queue. Schemes may not reveal, or may attempt to exaggerate, a prospective joiner's queue position which essentially means the scheme is a lottery. Some countries have ruled that matrix schemes are illegal on that basis.
Connection to multi-level marketing[edit]
Main article: Multi-level marketing
The network marketing or multi-level marketing (MLM) business has become associated with pyramid schemes. According to the U.S. Federal Trade Commission, many MLM schemes "simply use the product to hide their pyramid structure".[32] While some people call MLMs in general "pyramid selling,"[33][34][35][36][37] others use the term to denote an illegal pyramid scheme masquerading as an MLM.[38]
The Federal Trade Commission warns, "It’s best not to get involved in plans where the money you make is based primarily on the number of distributors you recruit and your sales to them, rather than on your sales to people outside the plan who intend to use the products."[39] It states that research is your best tool and gives eight steps to follow:
- Find—and study—the company’s track record.
- Learn about the product.
- Ask questions.
- Understand any restrictions.
- Talk to other distributors. Beware of shills.
- Consider using a friend or adviser as a neutral sounding board, or for a gut check.
- Take your time.
- Think about whether this plan suits your talents and goals.[39]
Some authorities contend that MLMs in general are nothing more than legalized pyramid schemes.[27][28][29][30]
Connection to franchise fraud[edit]
Main article: Franchise fraud
Franchise fraud (or "franchise churning") is defined by the U.S. Federal Bureau of Investigation as a pyramid scheme. The FBI website states:
One of Pearlasia Gamboa’s (president of the micronation of Melchizedek) franchise fraud schemes was described by the Italian newspaper La Repubblica as “one of the most diabolical international scams ever devised in recent years.”[41]
Notable recent cases[edit]
Internet[edit]
In 2003, the United States Federal Trade Commission (FTC) disclosed what it called an Internet-based "pyramid scam." Its complaint states that customers would pay a registration fee to join a program that called itself an "internet mall" and purchase a package of goods and services such as internet mail, and that the company offered "significant commissions" to consumers who purchased and resold the package. The FTC alleged that the company's program was instead and in reality a pyramid scheme that did not disclose that most consumers' money would be kept, and that it gave affiliates material that allowed them to scam others.[42]
WinCapita was a scheme run by Finnish criminals that involved about €100 million.
Others[edit]
The 1997 rebellion in Albania was partially motivated by the collapse of Ponzi schemes; however, they were widely referred to as pyramid schemes due to their prevalence in Albanian society.
In early 2006, Ireland was hit by a wave of schemes with major activity in Cork and Galway. Participants were asked to contribute €20,000 each to a "Liberty" scheme which followed the classic eight-ball model. Payments were made in Munich, Germany to skirt Irish tax laws concerning gifts. Spin-off schemes called "Speedball" and "People in Profit" prompted a number of violent incidents and calls were made by politicians to tighten existing legislation.[43] Ireland has launched a website to better educate consumers to pyramid schemes and other scams.[44]
On 12 November 2008, riots broke out in the municipalities of Pasto, Tumaco, Popayan and Santander de Quilichao, Colombia after the collapse of several pyramid schemes. Thousands of victims had invested their money in pyramids that promised them extraordinary interest rates. The lack of regulation laws allowed those pyramids to grow excessively during several years. Finally, after the riots, the Colombian government was forced to declare the country in a state of economic emergency to seize and stop those schemes. Several of the pyramid's managers were arrested, and are being prosecuted for the crime of "illegal massive money reception."[45]
The Kyiv Post reported on 26 November 2008 that American citizen Robert Fletcher (Robert T. Fletcher III; aka "Rob") was arrested by the SBU (Ukraine State Police) after being accused by Ukrainian investors of running a Ponzi scheme and associated pyramid scam netting US$20 million. (The Kiev Post also reports that some estimates are as high as US$150M.)
Throughout 2010 and 2011 a number of authorities around the world including the Australian Competition and Consumer Commission, the Bank of Namibia and the Central Bank of Lesotho have declared TVI Express to be a pyramid scheme. TVI Express, operated by Tarun Trikha from India has apparently recruited hundreds of thousands of "investors", very few of whom, it is reported, have recouped any of their investment.[46][47][48][49][50] In 2013, Tarun Trikha was arrested at the IGI Airport in New Delhi.[51]
In popular culture[edit]
- In The King of Queens episode entitled "Soft Touch", Doug gets sucked into a pyramid scheme when his persuasive neighbor recruits him to sell water filters.
- Stanton, a character of Charles Maturin's famous novel Melmoth the Wanderer, while put in Bedlam by his relative, finds a plan, written by some of his predecessors in the room he is placed. It is a plan of baptising all the population of Ottoman Empire, beginning with the Turkish ambassador, and is a classical pyramid scheme.
- The feature film Children of Invention tells the story of a mother who gets entangled in a pyramid scheme.
- The novel Welcome to the N.H.K. features a story arc wherein the main character is caught up in a crooked multi-level marketing scam called Mouse Road.
- On the NBC sitcom The Office, it is revealed that Michael did not attend college because he lost all his tuition money in a pyramid scheme. At a later date, the same character unintentionally attempts to recruit members of his staff into selling calling cards, not realizing that he had been conned into a pyramid scheme until it is made clear by an employee.
- Season one of the Channel 4 sitcom Peep Show, features an episode in which Jeremy becomes involved in a pyramid scheme after being ignorantly drawn into it by his neighbor Toni, whom he is trying to seduce.
- The 2010 film The Fighter features Dicky Eklund attempting a pyramid scheme to help pay for his brother's training.
- In two episodes of the sitcom Two and a Half Men entitled "Three Hookers and a Philly Cheesesteak" and "That Darn Priest", Alan runs a Ponzi scheme, targeting family and friends, in the name of his chiropractor business until Rose finds out and threatens to tell all his investors if he does not stop.
- In 2014, 62 artists in Brooklyn, New York created a pyramid scheme as new way of curating a contemporary art exhibit. "The Pyramid Scheme will not only reveal patterns and themes within contemporary art, but the social support structures which enable its creation."[52]
- In the King of the Hill episode entitled "Bill of Sales" Peggy gets caught up in a pyramid scheme.
- In the episode of The Simpsons titled "I Married Marge", Homer attends an investment seminar where the host introduces the 'Trapezoid Scheme' as an alternative to a Pyramid Scheme, before jumping out of a nearby window after hearing police sirens.
- In the episode of Kath & Kim titled "Money", Kath organizes a pyramid scheme lingerie party with Kim and Sharon modeling the merchandise so that Kath can raise enough money to pay for a pumpkin style coach for her upcoming wedding.
- In the It's Always Sunny in Philadelphia episode entitled "Mac and Dennis Buy a Timeshare", Sweet Dee begins selling for 'Invigaron', a multi-level marketing scam involving South American berries that bills itself as a 'Reverse Funnel System', using an upside-down triangle to demonstrate how it works. Frank points out to her that it's a pyramid scheme after telling her to turn the Reverse Funnel upside down.
See also[edit]
- Franchise fraud
- High-yield investment program
- Madoff investment scandal
- Claims of Social Security as a pyramid scheme
- Aman Futures Group
- Autosurf
- BurnLounge
- Cobra Group (company)
- Holiday Magic
- Lyoness
- Make Money Fast
- Nouveau Riche University
- Qnet
- Success University
http://en.wikipedia.org/wiki/Pyramid_scheme
http://www.ftc.gov/public-statements/1998/05/pyramid-schemes